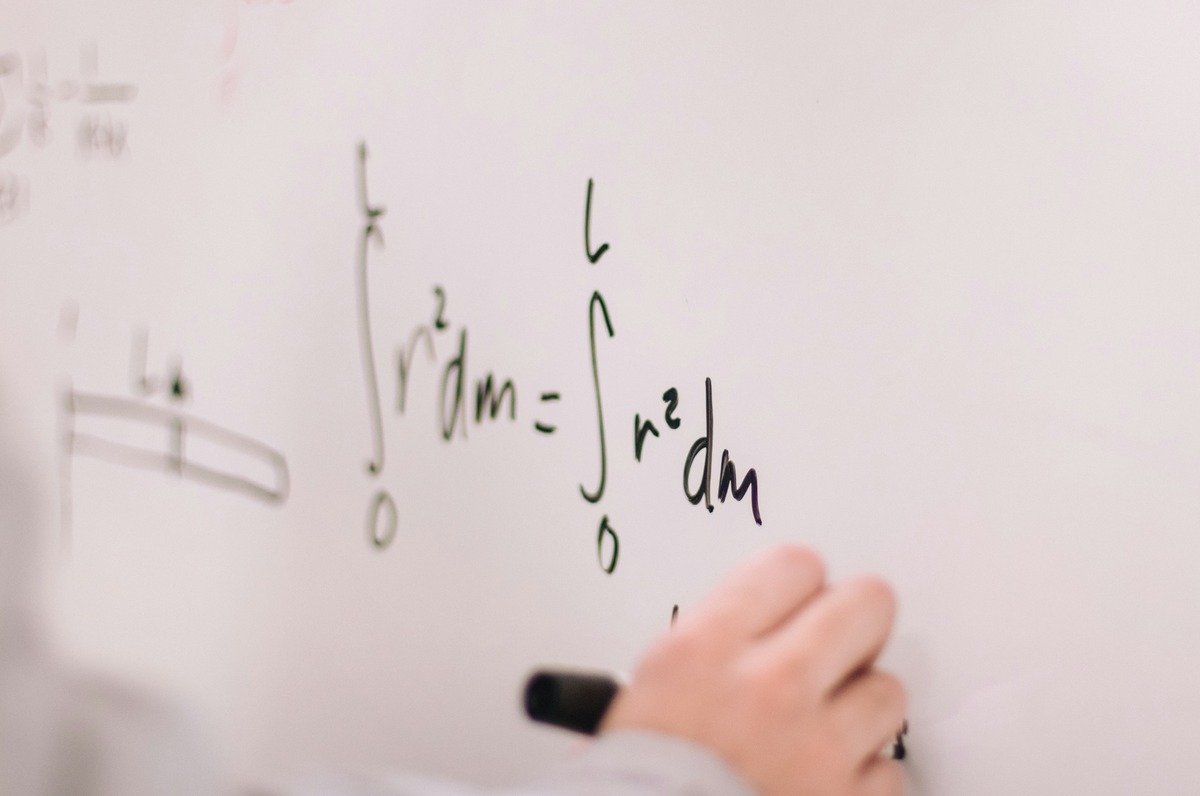Home> Technology and Computers
Technology and Computers
By: Donica Arbuckle • Technology and Computers
Discover The Truth: Is HDToday.TV Safe Or A Virus Trap?
Introduction When it comes to streaming movies and TV shows online, the quest for finding a reliable and safe platform is often riddled with uncertainty. HDToday.TV is one such platform that has garnered attention from entertainment enthusiasts seeking access to a vast array of content. However, the question that looms...
Read MoreBy: Nertie Boos • Technology and Computers
Emuparadise: The Truth About Viruses And Malware
Introduction Emuparadise has been a prominent name in the gaming community for years, providing a vast library of retro games and emulators. As with many popular websites, it has faced its fair share of controversies, particularly regarding the presence of viruses and malware within its files. This has sparked heated...
Read MoreBy: Stacia Brewington • Technology and Computers
Master The Art Of Identifying Concave Functions With These Simple Tips!
Introduction Understanding the concept of concave functions is paramount for anyone delving into the realm of mathematics and optimization. A concave function is a fundamental concept in calculus and optimization theory, playing a pivotal role in various fields such as economics, engineering, and computer science. Mastering the art of identifying...
Read MoreBy: Isobel Vandusen • Technology and Computers
The Ultimate Guide To Mastering The Scimitar In D&D – Unleash Your Inner Sword-Wielding Hero!
Introduction The scimitar, a graceful and deadly curved sword, has long been revered as a symbol of elegance and power. In the realm of Dungeons & Dragons (D&D), mastering the scimitar can elevate your character to legendary status, unleashing your inner sword-wielding hero. This ultimate guide is designed to equip...
Read MoreBy: Casie Diller • Technology and Computers
Unleash Your Power: Master The Art Of Booting People Offline!
Introduction In today's interconnected world, the ability to navigate and comprehend the intricacies of technology is a valuable skill. However, with this proficiency comes the responsibility to use it ethically and responsibly. The advent of the internet has revolutionized the way we communicate, work, and socialize, but it has also...
Read MoreBy: Hedvig Travers • Technology and Computers
The Shocking Reason Why This Number Is Restricted Or Unavailable!
Introduction Have you ever received a call from a number labeled as "Restricted" or "Unavailable" on your caller ID? This mysterious and enigmatic label often triggers curiosity and raises questions about the caller's identity and intentions. The prevalence of such calls has become a common phenomenon in today's interconnected world,...
Read MoreBy: Emyle Barry • Technology and Computers
Discover The Surprising Contrasts Between The Boeing 767 And 777!
Introduction When it comes to commercial aviation, the Boeing 767 and 777 stand out as two of the most iconic and widely utilized aircraft in the world. These twin-engine jets have left an indelible mark on the aviation industry, serving as the backbone of long-haul and mid-size routes for numerous...
Read MoreBy: Nerita Borges • Technology and Computers
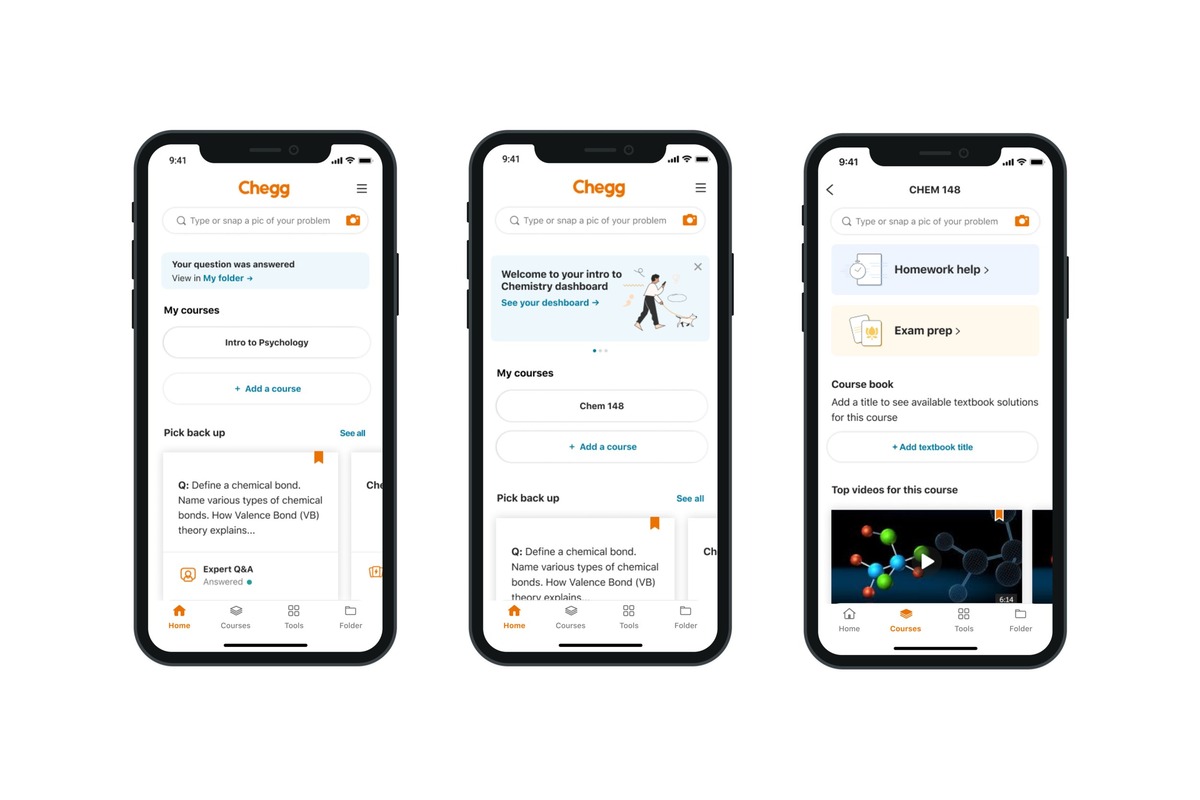
Unlock Chegg Answers Instantly With This Inspect Element Hack!
Introduction When it comes to academic success, students often seek assistance from various resources to overcome challenges and excel in their studies. One such popular resource is Chegg, a platform that provides a wide range of educational services, including textbook solutions, expert Q&A, and study support. However, accessing Chegg's comprehensive...
Read MoreBy: Marie Lodge • Technology and Computers
Facebook’s Epic Fail: Why Can’t They Filter Out Spam Comments?
Introduction Facebook, the social media giant that has connected billions of people worldwide, is facing a significant challenge – the proliferation of spam comments. These unsolicited and often irrelevant comments not only clutter users' feeds but also pose potential security risks and diminish the overall user experience. As Facebook strives...
Read MoreBy: • Technology and Computers
The Future of Linux in Education: Emerging Trends and Innovations
Linux, the open-source operating system that has long been a staple in the tech world, is on the cusp of a major transformation within the realm of education. As we hurtle toward an increasingly digital and interconnected world, the role of Linux in education is set to evolve in profound...
Read MoreBy: • Technology and Computers
Noodls x Sentiatechblog Tech Hub
Unveiling Tech Innovations Noodls.com is thrilled to unveil a significant enhancement to our technology and computers section with the introduction of SENTIATECHBLOG, a move underscored by our strategic acquisition of sentiatechblog.com. This acquisition not only expands our footprint in the digital realm but also brings a treasure trove of specialized...
Read MoreBy: Raye Decastro • Technology and Computers
A Better Way Of Receiving Emails Within End To End Testing
Introduction In the realm of end-to-end testing, ensuring the seamless functionality of email communications is paramount. Email testing plays a pivotal role in validating the complete flow of an application or system, encompassing user interactions, data processing, and the transmission of critical information. As technology continues to evolve, the traditional...
Read MoreBy: Cristi Wille • Technology and Computers
Imposter Syndrome How To Display Front End
Understanding Imposter Syndrome Imposter syndrome is a psychological pattern where individuals doubt their accomplishments and have a persistent fear of being exposed as a fraud, despite evidence of their competence. This phenomenon is prevalent in various professional fields, including front end development. Front end developers experiencing imposter syndrome may feel...
Read MoreBy: Mandy Spitzer • Technology and Computers
Re-Invent 2020 Day 4 Top 5 Announcements For Wednesday Friday
Introduction The highly anticipated Re-Invent 2020 event has been nothing short of exhilarating, with each day bringing forth a plethora of groundbreaking announcements and revelations. As we delve into the highlights of Day 4, we are met with a sense of anticipation and excitement, eager to uncover the latest developments...
Read MoreBy: Jocelin Sigmon • Technology and Computers
AWS Re-Invent 2020 Day 1 Top 5 Announcements
Keynote Address by Andy Jassy The much-anticipated AWS re:Invent 2020 kicked off with an electrifying keynote address by Andy Jassy, the CEO of Amazon Web Services. Jassy’s address set the tone for the event, unveiling a plethora of groundbreaking innovations and strategic initiatives that are poised to reshape the landscape...
Read MoreBy: Viv Sallee • Technology and Computers
AWS Re-Invent 2020 Day 2 AWS Is Coming To A Data Center Or Pizza Parlor Near
Keynote Address by Andy Jassy The much-anticipated AWS re:Invent 2020 kicked off with a captivating keynote address by Andy Jassy, the CEO of Amazon Web Services. With his characteristic passion and vision, Jassy set the stage for an exhilarating exploration of the latest advancements in cloud computing and technology. Jassy’s...
Read MoreBy: Marna Escalera • Technology and Computers
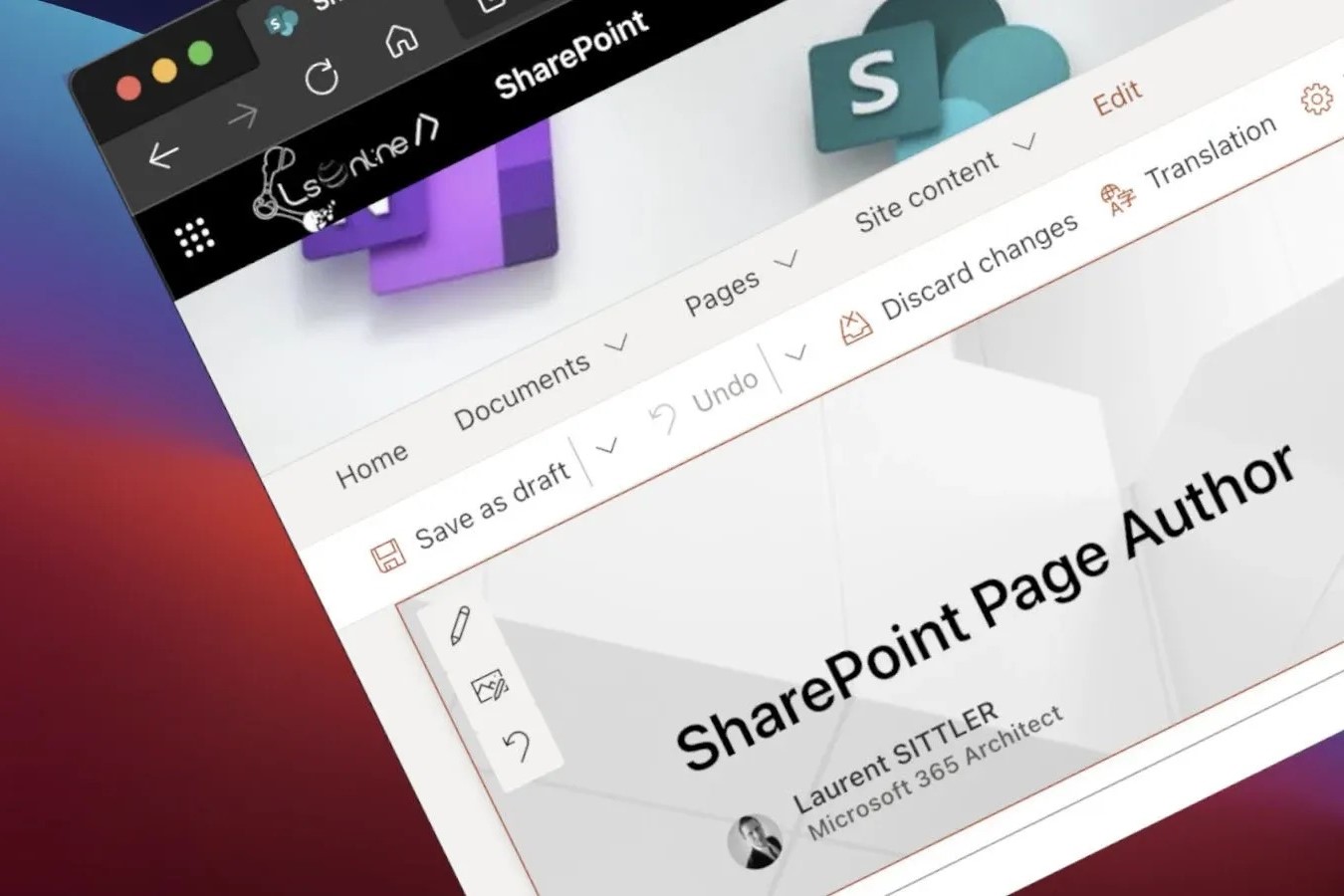
Creating A Custom Webpart For Sharepoint Online Pages
Introduction SharePoint Online, a cloud-based service hosted by Microsoft, offers a powerful platform for organizations to collaborate, manage content, and streamline business processes. One of the key features that sets SharePoint Online apart is its ability to customize and extend functionality through webparts. Webparts are reusable components that allow users...
Read MoreBy: Maryl Kipp • Technology and Computers
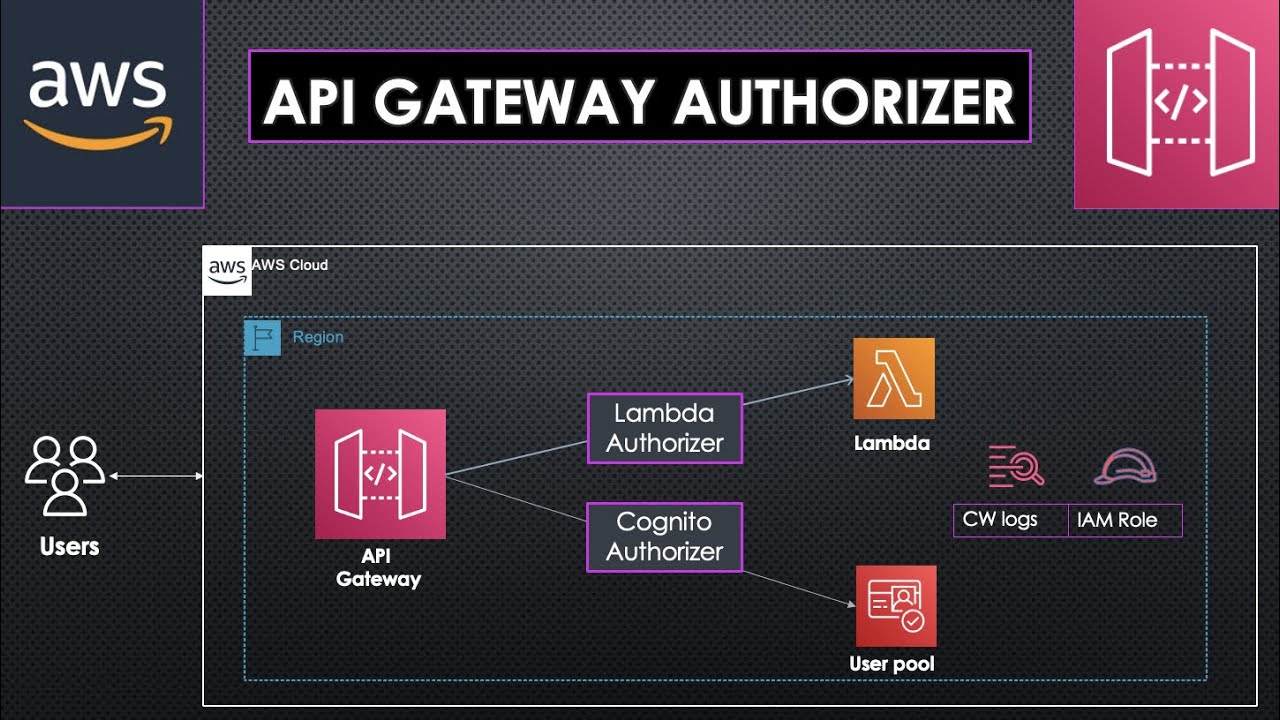
Serverless Basic Authentication Using A Custom Authorizer
Introduction In the world of web development, security is paramount. As technology advances, so do the methods of safeguarding sensitive information and ensuring that only authorized users have access to protected resources. One such method is serverless basic authentication using a custom authorizer. Serverless computing has gained significant traction in...
Read MoreBy: Vyky Henninger • Technology and Computers
Appsync Insights Part 2 Implementing A Generic String Filter In Python
Introduction In the fast-paced world of technology, the ability to harness and analyze data is paramount. As businesses strive to gain a competitive edge, the demand for efficient and versatile data filtering tools has surged. Appsync Insights, a powerful data analysis platform, has emerged as a game-changer in this domain....
Read MoreBy: Kelsi Moye • Technology and Computers
Ans Exercise 2 2 TCPDump Wireshark And Encapsulation
Introduction In the realm of technology and computer networks, the ability to analyze and interpret network traffic is paramount. This is where tools such as TCPDump and Wireshark come into play, offering invaluable insights into the intricate workings of data transmission and reception. By delving into the nitty-gritty of network...
Read MoreBy: Prudence Langlois • Technology and Computers
Using DCEVM Hotswap Agent In Java Development
Introduction In the world of Java development, efficiency and productivity are paramount. The ability to make code changes and see the results in real-time can significantly streamline the development process. This is where Dcevm Hotswap Agent comes into play. It is a powerful tool that enables developers to make changes...
Read MoreFeatured
By: Maurene Underwood • Entertainment
Unleashing The Power: The Secrets Behind Luffy’s Snakeman Gear 4
Read MoreBy: Courtnay Alford • Entertainment
Unleash The Power Of Tenser’s Transformation Against Rakshasa In D&D 5e!
Read MoreBy: Ansley Luciano • Entertainment
The Surprising Advantage Of Using A Light Crossbow In D&D 5e Revealed!
Read MoreBy: Rosalia Mcelwee • Featured
Mind-Blowing Temperature Conversion: 38.6°C To Fahrenheit Revealed!
Read More
PLEATED LAMPSHADE ARE MY NEW FAVORITE THING

SHOULD WE STAY LIGHT OR GO DARK WITH PAINTING OUR TINY MASTER BEDROOM?